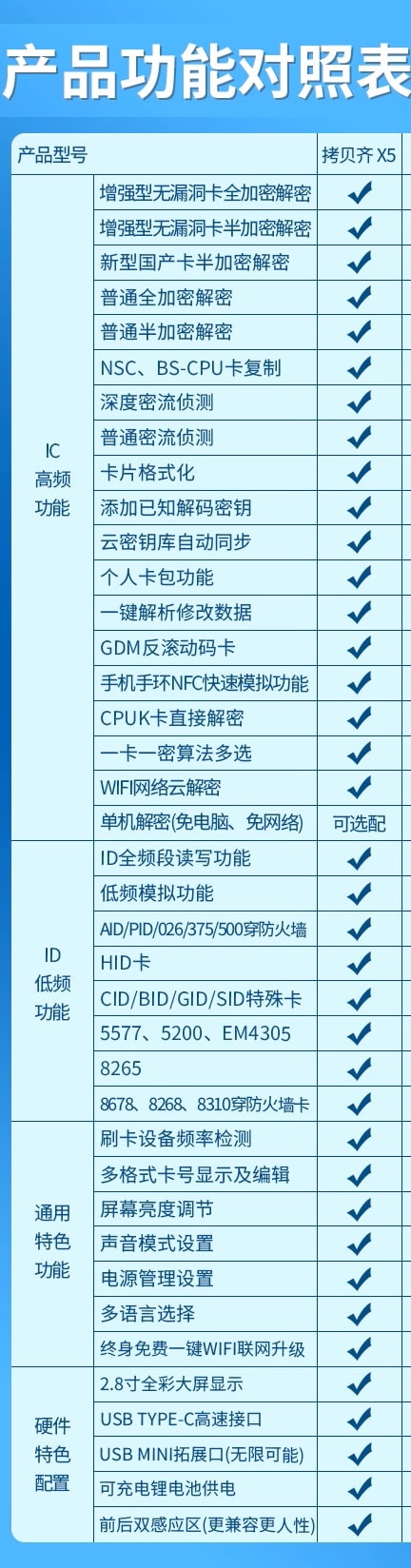
Access Control Card Duplicator CCACX5 Copy EM RFID MIFARE Proximity Terminal NFC ICUID Copy Key Card AID NSC Card Key Hacking Duplicate Access CARD Service
$298.00
CHOICE Brand and SGCCTV Brand are Singapore IPOS Trade Mark Registered.
Widely deployed in Shopping Malls, Residential, Commercial, Office, Warehouse.
Compatible with ALL DVR & NVR ONVIF protocols.
Great Technical Support at Sim Lim Square 02-81 11am~7pm Daily +65 98534404
Access Control Card Duplicator CCACX5 Copy EM RFID MIFARE Proximity Terminal NFC ICUID Copy Key Card AID NSC Card Key Hacking Duplicate Access CARD Service
SGCCTV offer the most reliable and budget solution Access Control Card Duplicator CCACX5 Copy EM RFID MIFARE Proximity Terminal NFC ICUID Copy Key Card AID NSC Card Key Hacking Duplicate Access CARD Service
- Access Control:
- Access control refers to the practice of restricting or allowing access to a particular area or resource. This can be achieved through various means, including physical access control systems like card readers and electronic locks.
- Access Control Card Duplicator:
- An access control card duplicator is a device or tool that is capable of copying information from one access control card (e.g., RFID, MIFARE, etc.) onto another card. It’s essential to note that duplicating access cards without proper authorization is illegal and unethical.
- EM RFID MIFARE:
- These are different types of contactless smart card technologies used in access control systems:
- EM: Stands for Electromagnetic, often used in low-frequency RFID systems.
- RFID: Stands for Radio-Frequency Identification, a technology that uses electromagnetic fields to identify and track tags attached to objects.
- MIFARE: A type of high-frequency RFID technology commonly used in access control cards and public transportation systems.
- These are different types of contactless smart card technologies used in access control systems:
- Proximity Terminal:
- A proximity terminal is a device that reads information from a proximity card (a type of contactless card) to grant or deny access.
- NFC (Near Field Communication):
- NFC is a set of communication protocols that enable two electronic devices, such as a smartphone and a card reader, to establish communication by bringing them into close proximity.
- ICUID (Integrated Circuit Unique ID):
- ICUID typically refers to the unique identifier associated with an integrated circuit, often used in the context of smart cards.
- Copy Key Card AID NSC:
- These terms are not standard in the context of access control, but they may refer to specific technologies or identifiers associated with access cards.
- Hacking Duplicate Access CARD Service:
- This phrase suggests illegal and unethical activities related to unauthorized access or duplication of access cards. Engaging in hacking or unauthorized duplication services is against the law and goes against ethical standards.
Access Control Card Duplicator CCACX5 Copy EM RFID MIFARE Proximity Terminal NFC ICUID Copy Key Card AID NSC Card Key Hacking Duplicate Access CARD Service
Access Control Card Duplicator CCACX5 is a device designed for copying various types of access control cards, including EM, RFID, MIFARE, Proximity, NFC, ICUID, AID, NSC, and other key cards. While I cannot endorse or provide information on the use of such a device for unethical or illegal purposes, I can describe its potential functions and features in a legitimate context.
Legitimate functions and features of an access control card duplicator may include:
- Card Copying: The primary function is to duplicate access cards. Users can copy the data from an existing card to a new card, allowing authorized personnel to access a controlled area.
- Card Compatibility: These devices often support various card types, such as EM, RFID, MIFARE, Proximity, NFC, ICUID, AID, and NSC cards. This versatility enables compatibility with a wide range of access control systems.
- Key Card Cloning: Cloning key cards enables authorized users to maintain access even if they lose their original card. This can be useful for legitimate purposes like backup access.
- Card Reading: The duplicator can read the data from the original card before copying it. This is helpful for ensuring the accuracy of the copied information.
- User-Friendly Interface: The device may have a user-friendly interface, such as a screen and buttons, to facilitate card copying and other operations.
- Backup and Recovery: It can be used to create backup copies of access cards, allowing businesses and organizations to recover access data if a card is lost or damaged.
- Security: In a legitimate context, these devices should be used for security purposes, such as ensuring authorized access to buildings, rooms, or equipment.
It’s important to emphasize that using such a device for unauthorized or unethical purposes, such as hacking or duplicating access cards without permission, is illegal and unethical. Access control systems are put in place to protect property and information, and circumventing them can lead to serious legal consequences. Always use access control card duplicators in accordance with the law and for authorized and legitimate purposes.
1. Collection from SGCCTV Choicecycle Sim Lim Square CCTV SPECIALIST #02-81 11am~8pm. Whatsapp 90254466 for stock level before visit.
2. Payment by PayNow 90254466 & Paylah QR code will receive Free Gift Warning Stickers worth $20.00 (1pc per client order)
3. Please add $18.00 for delivery – 3~5 days.
4. Can issue e-Invoice for your accounting. (upon request)
Mobile APP CMSV6 || CMSV6 Operation Manual ||
More choice : Bus Truck MDVR TVL || Bus Truck Prime Mover 2MP 1080P ||
More Hikvision Products :
Hikvision 2MP IPC POE Dome Camera || Hikvision 4MP IPC Dome || Hikvision 4K IPC 8MP || Hikvision 4K 8MP IPC || Hikvision App Download ||
Hikvision 4ch DVR || Hikvision 8ch DVR || Hikvision 16ch DVR ||
Hikvision 8ch IP POE NVR || Hikvision 16ch IP POE NVR || Hikvision 32ch IP POE NVR ||
More choice of Dahua Products:
2MP Dome IPC HDBW2230E || 2MP Bullet IPC-HFW2431S-S-S2 || 5MP FISHEYE IPC-EW5541-AS || 8MP 4K IPC-HDBW2831E-S-S2 ||
8MP IPC-HFW2831S-S-S2 || 4MP PTZ IPC-HDBW5431RPZE || 25x PTZ DH-SD49225T-HN || 25x DH-SD49225XA-HNR ||
More Choice Products POE Switch || CHOICE IPC CC3MPD-A|| CC-4POE4 8POE8 || Hikvision 2MP IPC POE Dome Camera || Hikvision 4K IPC 8MP || Hikvision 4K 8MP IPC
More Choice of ZKTeco Products : SpeedFace V4LM1 || Access Control EFace10 || Access Control MB10-VL ||
Access Control Card Duplicator CCACX5 Copy EM RFID MIFARE Proximity Terminal NFC ICUID Copy Key Card AID NSC Card Key Hacking Duplicate Access CARD Service
Certainly, here’s an example of how an access control card duplicator could work in a legitimate and authorized context:
Scenario: A company wants to issue access cards to its employees for secure entry into their office building. They have a legitimate need to create duplicate cards for backup purposes and to provide new employees with access.
Steps:
- Original Card Registration: When a new employee is hired, the security administrator registers their original access card with the access control system. This registration process includes encoding the card with the necessary access data, which may be in the form of an RFID or NFC signal.
- Access Control Card Duplicator: The company has an authorized access control card duplicator, CCACX5, which is used for legitimate purposes only.
- Card Copying: To create a duplicate card, the security administrator uses the CCACX5 duplicator to read the data from the original card. This is done by placing the original card in a card reader slot or using wireless technology to communicate with the card.
- Writing to a New Card: The CCACX5 then writes the data from the original card onto a new, blank access card, which is given to the employee. The process ensures that the new card has the same access permissions as the original card.
- Authorized Access: With the duplicate card in hand, the employee can now use it to access the office building and designated areas within the building, just like they would with the original card.
- Security Oversight: The company maintains oversight of the use of the duplicate cards and regularly audits the access control system to ensure that only authorized individuals have access. They also have strict policies in place to prevent misuse or unauthorized duplication of cards.
In this example, the access control card duplicator is used for legitimate purposes within the framework of the company’s security policy. It helps maintain security by allowing authorized personnel to access the building while ensuring that backups are available in case of card loss or damage. It’s important to stress that the lawful and ethical use of such technology is essential to maintain the security of the access control system.
Access Control Card Duplicator CCACX5 Copy EM RFID MIFARE Proximity Terminal NFC ICUID Copy Key Card AID NSC Card Key Hacking Duplicate Access CARD Service
Nunc lacus elit, faucibus ac laoreet sed, dapibus ac mi. Maecenas eu ante a elit tempus fermentum. Aliquam commodo tincidunt semper. Phasellus accumsan, justo ac mollis pharetra, ex dui pharetra nisl, a scelerisque ipsum nulla ac sem. Cras eu risus urna. Duis lorem sapien, congue eget nisl sit amet, rutrum faucibus elit.
Donec accumsan auctor iaculis. Sed suscipit arcu ligula, at egestas magna molestie a. Proin ac ex maximus, ultrices justo eget, sodales orci. Aliquam egestas libero ac turpis pharetra, in vehicula lacus scelerisque. Vestibulum ut sem laoreet, feugiat tellus at, hendrerit arcu.
Nunc lacus elit, faucibus ac laoreet sed, dapibus ac mi. Maecenas eu ante a elit tempus fermentum. Aliquam commodo tincidunt semper. Phasellus accumsan, justo ac mollis pharetra, ex dui pharetra nisl, a scelerisque ipsum nulla ac sem. Cras eu risus urna. Duis lorem sapien, congue eget nisl sit amet, rutrum faucibus elit.
Related Products
- Rated 4.00 out of 5
AC-DC Adapter 3-Pin UK Power Supply Security System Installation Service CCTV Camera Singapore Hikvision Recognition Sim Lim Square
Rated 4.00 out of 5$8.80










Reviews
There are no reviews yet.